Recently I had to do an installation of Fortinet Fortigate VMX 6.* on a small cluster that already was running NSX. Since there is hardly any documentation on it besides an older pdf from Fortinet I decided to document my own following of that document.
Since my lab’s still on 6.5 I decided to do everything within the flash client of vCenter.
Disclaimer: I am not a Networking or Security professional so there’s a good chance I am not keeping to some standards in those worlds.
What you need
- both Fortigate vmx ovf files with vmdk’s for version 6.*
- Webserver with anonymous access for the deployment of the security vm’s
- NSX already pre-installed
Setting up the VMX Manager
First you start with deploying the VMX Service Manager from vSphere. It’s important that note that there are two ovf files. One for the Service Manager and one for the Security VM. You need the FortiGate-VMX-Service-Manager.ovf first. During this deployment you need to select two networks. One for management and a sync network. The latter is for communication with the security vm’s only so can be non-routed. It is possible to have a dhcp server running in this vlan as long as it doesn’t provide a default gateway (Servers don’t like multiple gateways. capiche?). For the security vm’s the service manager is able to act as dhcp for the security vm’s. Since I use this vlan for more things I have dhcp running on my domain controller but will set a static ip on the service manager.


When the deployment has finished you can power the VM on and you need to open the console for some commands. Please note that I added the extra end’s to the commands compared to the manual.
Somehow they put the ip config in the ovf but that doesn’t work so you need to set it manually
config global
config system interface
edit mgmt
set ip <IP address for the MGMT interface > <subnet mask>
set allowaccess ping https ssh http
end
end

Now we need to configure the default gateway
config vdom
edit root
config router static
edit 0
set device mgmt
set gateway <IP address of gateway>
end
end

and configure dns ( I only have 1 dns host)
config global
config system dns
set primary <IPv4 address of DNS server>
set secondary <IPv4 address of DNS server>
end
end

So the basic configuration has been done and we should have access to the web interface by now. Just regular https on port 443. Default is admin without password.

If you want you can change the password now (recommended!!)

You’ll see a dashboard similar to this but with an evaluation license.

If you click on FGTVMX License you’ll get a button to install the license.

Click on upload and click ok to install the license, the VMX Service Manager will reboot after this.

With this done we need to set some default settings under Global > System > Settings

Since I only have my Domain Controller for ntp I need to do this from the CLI
config global
config system ntp
set type custom
config ntpserver
edit 0
set server <IPv4 address of NTP server>
end
end
end

and the result

Connecting with NSX
Here we find one of the bigger changes with the manuals of the 5.* releases of Fortigate VMX.
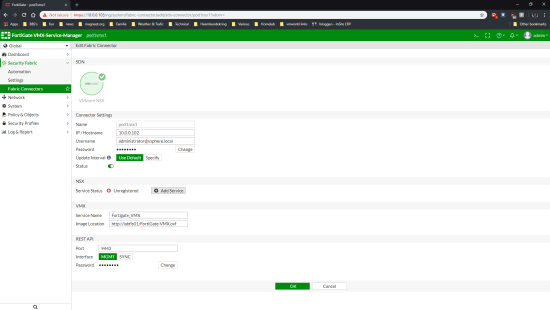
The 6.* releases of Fortigate VMX already come with the NSX service installed so the only thing we need to do is register the VMware NSX SDN. This can be done under Global>Dashboard>Security Fabric> Fabric Connectors.

Fill in all the fields, the image location has to be an anonymous 🙁 webserver that has both the vmdk files and the ovf. Click on ok when you are done.

Now we need to edit the connector again to register the service. Select the NSX Connector and click on edit.

Hit the Add Service button and the service will be created for you (previously this had to be done from the cli)

If you now go to the Service Definitions in NSX it will show an Extra one called Fortigate_VMX or whatever you named it.

Configuring NSX for Fortigate VMX
Next thing to do is to create a service deployment. Click on add on the Service Deployment tab under Networking & Security > Installation and Upgrade.

Select the Fortigate service name
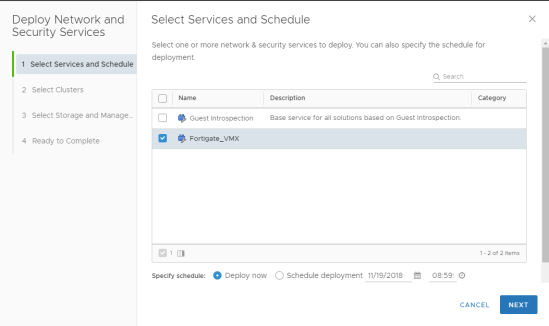
Select the cluster where you want to deploy Fortigate VMX

Select the datastore where the Service VM’s need to be placed, the correct portgroup and if you want to use dhcp or an ip pool for the service vm’s.


and finally click finish

NSX will now start deploying the service vm’s. Usually it creates a new resource pool for these but that somehow failed for me.


Next up is creating Security groups for the vm’s that we need to firewall. This is done in the service manager for NSX.
Click add

Choose a name

Choose a rule for when vm’s are a member of this group

I didn’t use the next 2


And hit finish

The group now consists of several of my VDI Desktops

Last but not least we need to create a redirection policy.
Under service composer > security policies click add

Choose a name

skip Guest introspection and firewall rules. Under Network Introspection click add

Choose a name and select the direction of the traffic that gets filtered within the group where this gets applied.

I created two service for all incoming traffic to my security groups and all outgoing.

click next & finish.
Now click on the newly created security policy

click Apply

Select the security group where you want to apply the policy, put it in selected objects and click apply.

With this traffic should be redirected to Fortigate VMX and the firewalling can be setup over there.









































































